Google is the encyclopedia of the internet that carries the response to all your thoughts and curiosity. Immediately after all, it is just a world-wide-web index to come across pictures, articles or blog posts, and video clips, appropriate?
Properly, if you think so, you are turning a blind eye to the untapped probable of the behemoth lookup engine’s crawling abilities. This facet of Google is lesser-recognised to the typical consumer but propelled efficiently by lousy actors to hijack websites and steal sensitive information from corporations.
Right here, we will handle how safety industry experts and hackers use Google as an successful reconnaissance resource to entry sensitive details, hijack internet sites, and more.
What Is Google Dorking?
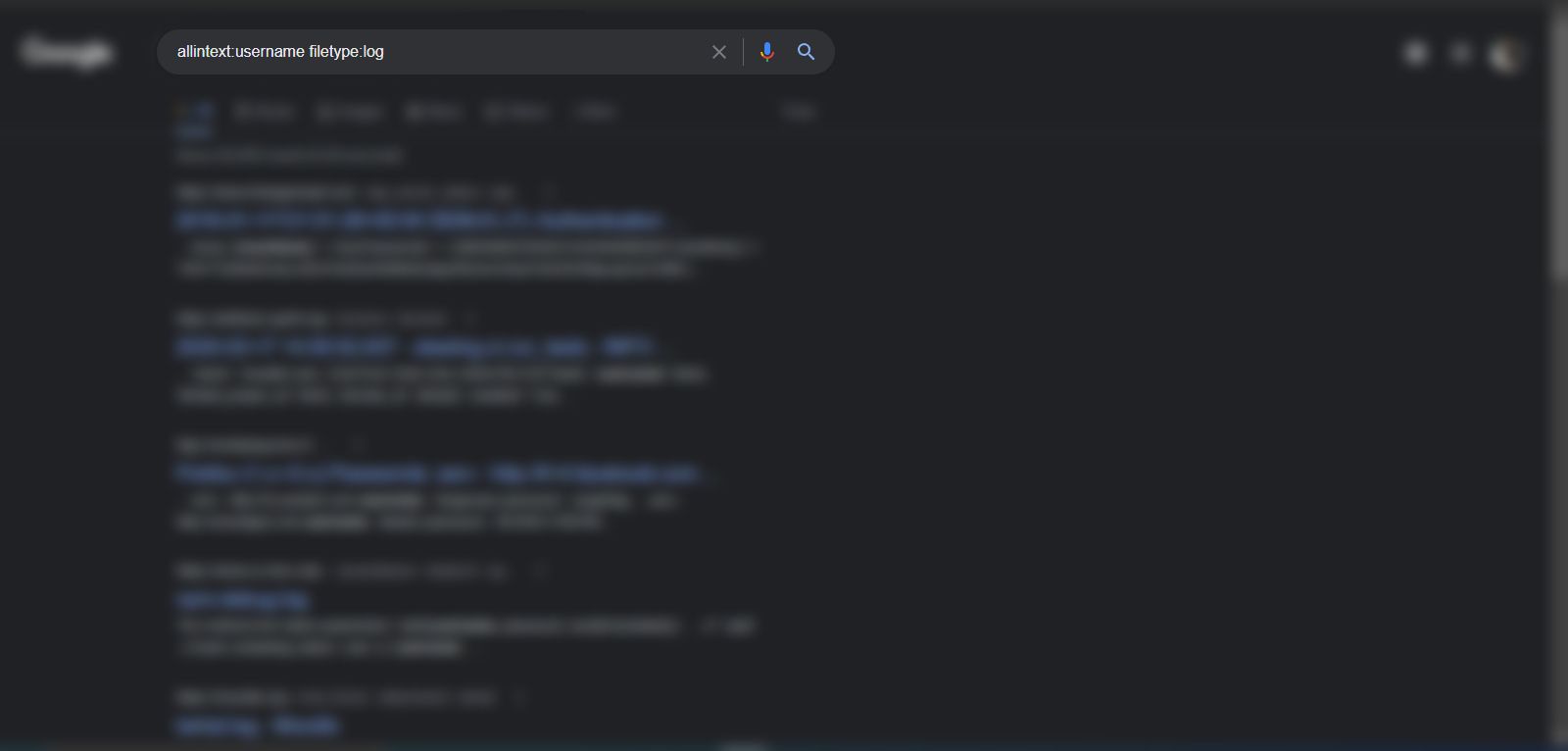
Google dorking or Google hacking is the system of feeding highly developed search queries into the Google look for motor to hunt for delicate details these kinds of as username, password, log files, and many others., of websites that Google is indexing thanks to web-site misconfiguration. This facts is publicly visible and, in some scenarios, downloadable.
A standard Google search requires a seed search phrase, sentence, or dilemma. But, in Google dorking, an attacker makes use of specific operators to enrich research and dictate the internet crawler to snipe for really specific information or directories on the world-wide-web. In most situations, they are log files or web-site misconfigurations.
How Hackers Use Google Dorking to Hack Web sites
Google dorking will involve employing specific parameters and search operators identified as “dorks” to narrow down search final results and hunt for uncovered delicate knowledge and safety loopholes in internet websites.
The parameters and operators immediate the crawler to appear for distinct file forms in any specified URL. The search outcomes of the query consist of but are not limited to:
- Open up FTP servers.
- A company’s interior files.
- Obtainable IP cameras.
- Government paperwork.
- Server log information containing passwords and other delicate knowledge that can be leveraged to infiltrate or disrupt an business.
Most-Applied Google Dorking Operators
Even though there are tons of operators and parameters that a single can utilize to a search query, it only requires a handful of them to serve the requirements of a security skilled. Right here are a couple frequently applied queries:
- inurl: Dictates the crawler to lookup for URLs that comprise a specified search term.
- allintext: This parameter lookups for consumer-specified textual content in a webpage.
- filetype: This parameter tells the crawler to look for and display screen a distinct file type.
- intitle: Scrapes for websites that contains specified search phrases in the title.
- web-site: Lists all the indexed URLs for the specified web page.
- cache: When paired with the web site parameter, this a single shows the cached or more mature variation of a web site.
- Pipe operator (|): This rational operator will list results that have both of two specified lookup phrases.
- Wildcard operator (*): This is a wildcard operator that searches for webpages that include everything linked to your search term.
- Subtract operator (-): This gets rid of unwanted outcomes from your lookup.
Is Google Dorking Illegal?
Even though it may appear to be daunting, Google dorking will not land you guiding bars, offered you are only applying it to refine your lookup effects and not infiltrate an corporation.
It is a important evil and, in simple fact, an inspired observe amongst electricity buyers. Hold in intellect that Google is monitoring your lookups all the time, so if you access delicate details or look for with malicious intent, Google will flag you as a menace actor.
In situation you are carrying out a pen exam or searching for bug bounty, make certain that you are completely approved and backed by the group. Usually, if you get caught, points can acquire a change for the worst, and 1 can even slap you with a lawsuit.
How to Secure Your Site From Google Hacking
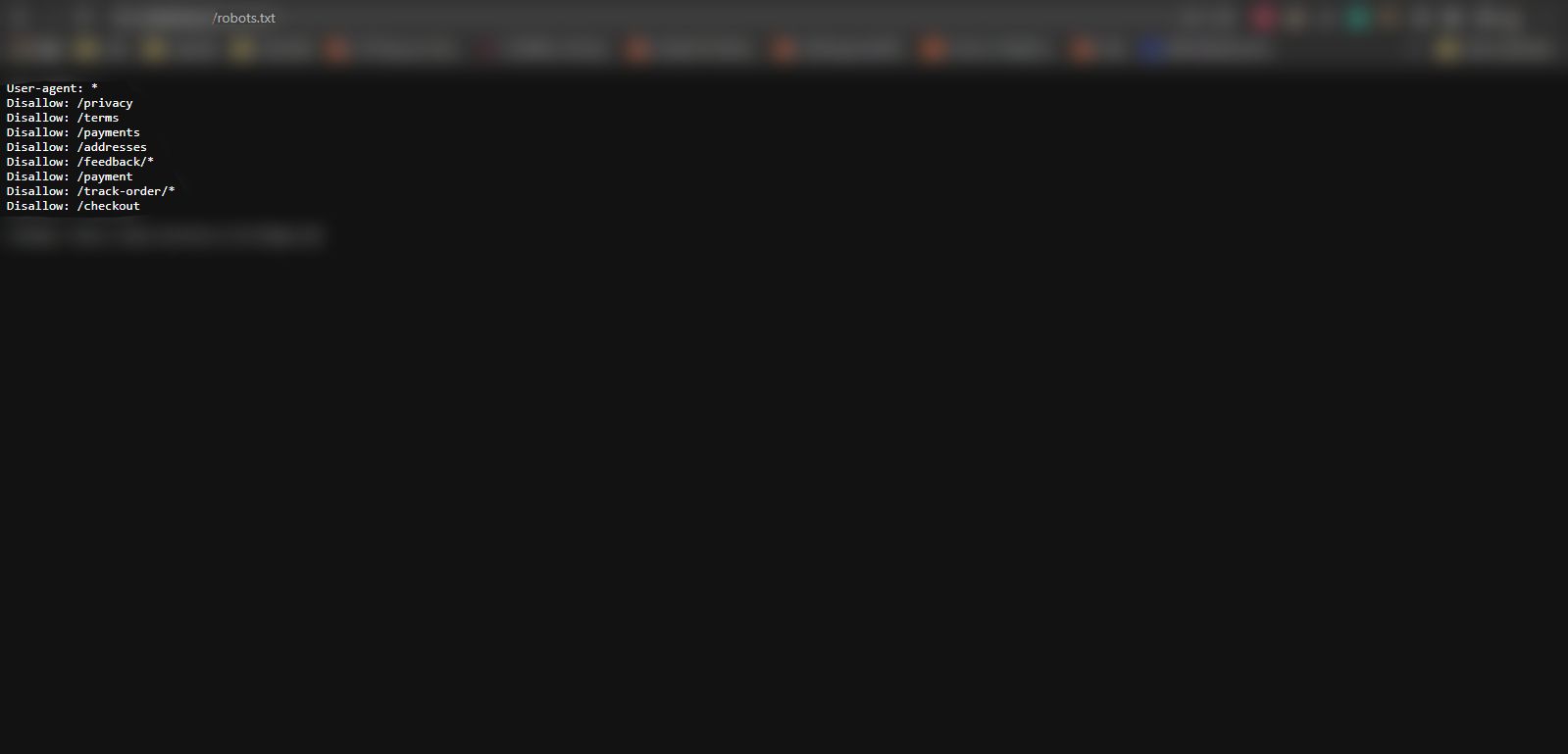
As a webmaster, you have to set up particular defensive countermeasures to deal with Google Dorking. A incredibly simple tactic would be to incorporate a robots.txt file and disallow obtain to all delicate directories. This will preserve lookup engine crawlers from indexing delicate files, directories, and URLs as you checklist them.
Adding a robots.txt file to the root listing is a basic superior observe and important for the general safety of your site. Discover more about why web page protection is vital.
Other means to mitigate this risk would be to encrypt delicate info such as usernames, passwords, payment info, and so forth., and use Google Look for Console to clear away web pages from search success.
Turn into a Google Electricity Consumer With Google Dorking
Though most of us use Google each day, we rarely ever choose advantage of its true possible. You can harness the typically-neglected electrical power of Google dorking ethically to refine your Google-fu and come across just about everything on the world wide web.
With the good parameters and search phrases in area, the response to all your curiosities and questions will lie at your fingertips, just a person keypress absent. Study far more about the most effective guidelines and tips to make the most of your Google look for.



/cdn.vox-cdn.com/uploads/chorus_image/image/62810996/Amm_DeepSentinel_01.0.jpg)

More Stories
Benefits and Pros vs Cons – Moosmosis
Steve Hargadon: New Dr. Albrecht Library 2.0 Podcast: “DEI and BELONGING”
Spark Student Creativity with Handmade Gifts